I am not responsible for misuse of this information.
This article describes how computer networks can be hacked remotely using telnet. It will give you the basic idea behind how this is done.
Hackers always do things remotely. One of the oldest and most efficient ways is telnet. For the purpose of making this easy to understand, lets assume the following. A hacker located at point 1 in Georgia wants to hack a computer system located in Canada (point 5). In order to reduce his/her chances of getting caught, the hacker would pick a public place in georgia to start from. This place would be somewhere that is accessible to everyone such as a library. The hacker would then open telnet and remotely login to a computer system (point 2) in Oregon. Next he/she will spawn a connection to another machine or network (point 3) located in Nebraska. Next, the hacker will make a huge jump and make another connection overseas to network in Poland (point 4). Finally, the hacker goes in for the kill and Connects to their target network located in Canada (point 5), and does some damage.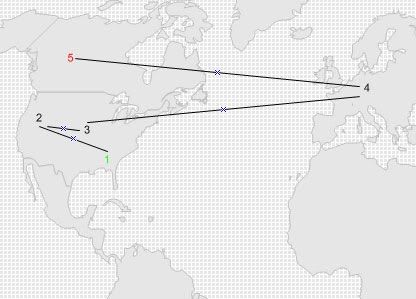
What Happens Next?
The SA's (systems administrators) for the network in Canada realizes the system was hacked. They trace the connection to Poland. After talking to the SA there, they realized the hacker was not even located in Poland. This is a process known as "backtracking." A good hacker will choose his/her connection points carefully to make backtracking complicated or most of the time impossible. The best connection points are often normal machines owned by home users. This is because the average home user does not keep logs of connections to their machine. If a hacker hops through several machines that have no logging system at all, the backtracking quickly comes up empty.
Most telnet servers give you the ability to "telnet out." This means that you are using the telnet server as an access point to reach your destination or target.
 Remember that telnet can run on all different devices. Most servers are now using SSH instead of telnet because it is more secure. In my opinion, the best source for telnet "hopping" is a router or switch. This is because routers and switches are usually not monitored as closely as servers or workstations. The logging system of a server can be complicated. In some cases, logging systems can span across multiple machines and backup devices on a network. Generally, there is a much greater chance someone will notice you logged into a server than a router or switch. All high-end routers like Cisco, 3com, Nortel and even some lower-end products run telnet. The easy way to find these devices is to port scan. If you conduct a scan of a network and find port 23 active, it's a telnet server.
Remember that telnet can run on all different devices. Most servers are now using SSH instead of telnet because it is more secure. In my opinion, the best source for telnet "hopping" is a router or switch. This is because routers and switches are usually not monitored as closely as servers or workstations. The logging system of a server can be complicated. In some cases, logging systems can span across multiple machines and backup devices on a network. Generally, there is a much greater chance someone will notice you logged into a server than a router or switch. All high-end routers like Cisco, 3com, Nortel and even some lower-end products run telnet. The easy way to find these devices is to port scan. If you conduct a scan of a network and find port 23 active, it's a telnet server.Now What?
The idea behind using a telnet server to connect to other systems is to hide your real IP address. The IP addresses used in this article are not real, but still represent the concept accurately. If you connect to your target (129.125.243.5), the address logged would be the telnet server (192.168.1.1), not your real IP address (192.168.0.2). Remember, the more telnet servers you hop through, the better. Using 1 telnet server does next to nothing because your ISP most likely has a record of what telnet sessions you have connected to and could make a match from both ends. Believe me you would be surprised what your ISP can find out. Some say that they only track your bandwidth usage, but with Carnivor working at most ISP's they can dig up almost anything. The safest way to connect to devices is to establish a connection to an SSH server first. From there, any connections made from an SSH server would be undetectable by an ISP because SSH uses secure channels. Your ISP would only be able to tell that you were connected to an SSH server, and not what you were actually doing with that server. High-profile hacks are very complicated and can span across multiple devices (as many as hundreds) making it impossible to track the source IP address. Often times a hacker will use a dial-up account (that isn't theirs) or a public location, hop through telnet devices and make their attack. The image below shows a digram of the connections I discussed above.
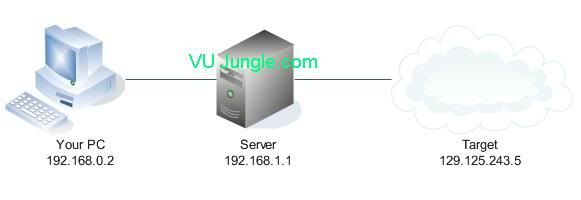
Public Telnet Servers
There are public telnet servers available for many different reasons. Some are for chatting, news, email, etc. They are not as common now because we have better ways of doing things now (HTTP, FTP, AIM, etc). Most of the public servers will not allow you to telnet out. However, there are still some out there. Although, using a route-server is a really bad idea because an ISP has the ability to log EVERYTHING! Some route-servers even advertise the fact that they log everything.
Conclusion
Remember that all these devices have logging capabilities. Logs are the easiest way to track someone. However, a good hacker will know how to manipulate or clear the logs to "clean up." Also, using a telnet device to remotely access a target is not the same as a DoS attack. While they are both viewed as malicious activity, they are not synonymous.



0 comments:
Post a Comment