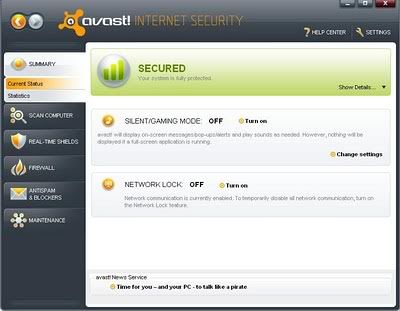
Avast! provides a package of applications that aim to protect your computer from a possible virus infection or other malware threat. If you use it correctly, and in combination with other programs such as data backup utilities, it will significantly reduce the risk of your computer being attacked or infected by a virus, and thus the risk of losing important or private data.
The Avast! Internet Security application comes with an antispam filter and built-in firewall. Once installed, avast! runs silently in the background to protect your computer against all known forms of malware. You dont need to do anything else - just install and forget! Active internet users need greater protection for themselves as they shop and bank on-line. To secure against threats from infected web sites and the growing risk of identity theft, avast internet security provides you with continuous protection from its layers of antivirus, anti-spyware, anti-rootkit protection, firewall and antispam.
Real-time shields. The real-time shields are the most important part of the program, as they are working continuously to prevent your computer from becoming infected. They monitor all your computers activity, checking all programs and files in real-time - i.e. at the moment a program is started or whenever a file is opened or closed.
Virus Chest. The virus chest can be thought of as a folder on your hard disk with special properties, that make it a safe, isolated place for storing potentially harmful files. You can work with the files in the virus chest, with some security restrictions.
avast! antispam filter. avast! Internet Security includes a fully integrated antispam filter to detect unwanted email.
Spam delivered to your mailbox can result in your mailbox quickly becoming full, as a result which, legitimate emails may not be received. It can also unnecessarily increase the load on the email server, internet connection, local networks etc.
Firewall. avast! Internet Security includes a fully integrated firewall which can be controlled directly from the avast! user interface.
The firewall monitors all communication between your computer and the outside world and blocks unauthorized communication based on a number of "allow" and "deny" rules. In this way, the firewall can prevent sensitive data from leaving your computer and can also block attempted intrusions by external hackers
Command-line scanner. The ashCmd program uses the same avast! scanning engine to detect potential malware infections so the results are exactly the same as running a scan via the normal program interface. The avast! command-line scanner, ashCmd.exe, is normally installed in the directory C:Program FilesAlwil Softwareavast5.
A scan is run from the command prompt using various switches and parameters. To see a description of the parameters, locate the ashCmd file and double click on it. This will open a new window in which the various parameters are displayed.
* Continuous protection against viruses and spyware
* Ensures all mails sent and received are clean
* Keeps you protected from "chat" infections
* Stops attacks from hijacked websites
* Lets you safely browse suspicious websites or run unknown applications
* Blocks hacker attacks to protect your identity
* Keeps your mailbox free from spam
* Allows safe and uninterrupted gaming
* Compatible with Windows XP, Vista and 7
Key technologies:
* Improved Antivirus and anti-spyware engine
* New avast! Sandbox
* New Silent Firewall
* New Antispam
* NewBehavior Shield
* New avast! Intelligent Scanner
* New Silent/Gaming Mode
* Real time anti-rootkit protection
* avast! Community IQ
* Behavioral Honeypots
* Smart virus updates
* Green computing
* avast! iTrack
* File System / Mail Shield
* Web Shield
* IM / P2P Shield
* Network Shield
* Script Shield
Download:
http://www.mediafire.com/?kvrwndria1o








 Disclaimer: It is not recommended to edit the registry without proper Knowledge. I don't guarantee that this will work for everyone.Do this at your own Risk.
Disclaimer: It is not recommended to edit the registry without proper Knowledge. I don't guarantee that this will work for everyone.Do this at your own Risk.

